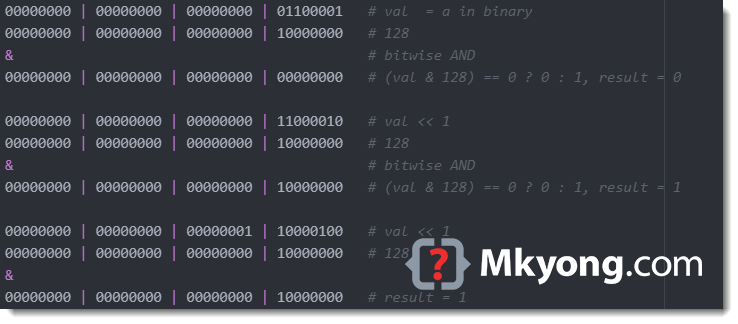
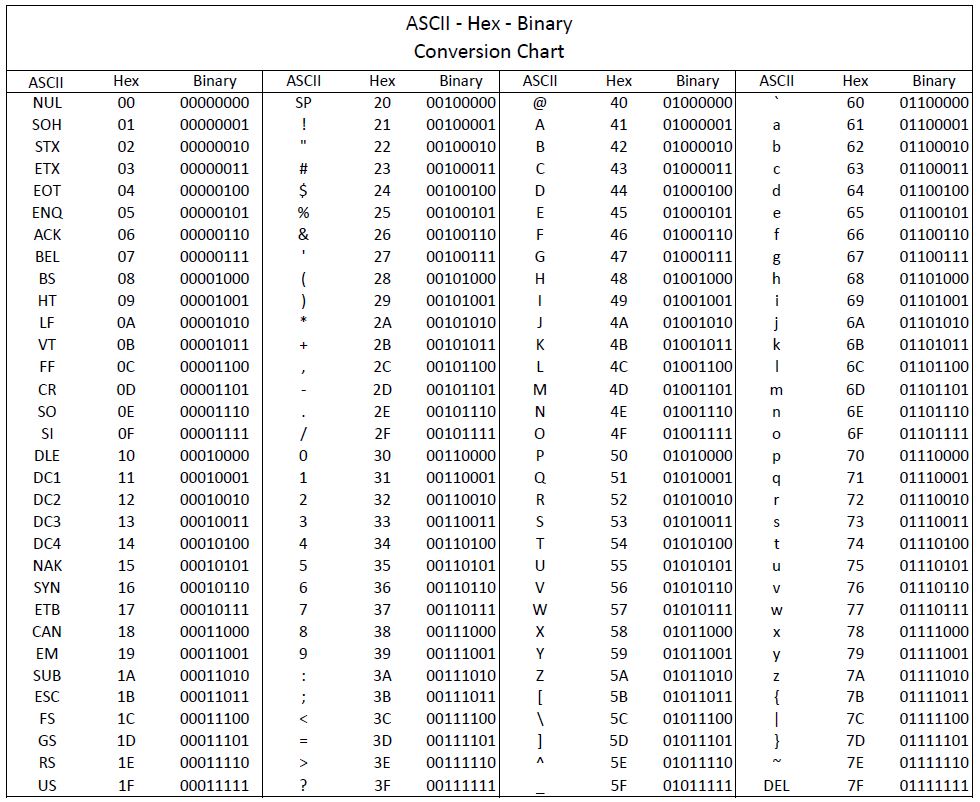
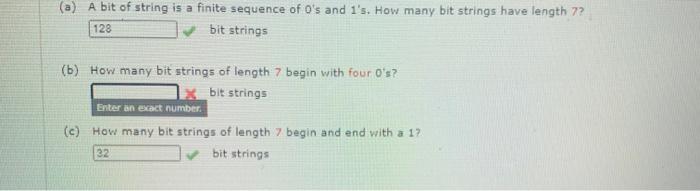
Igor's Tip of the Week #128: Strings list - Malware Analysis - Malware Analysis, News and Indicators

What's the deal with encryption strength —is 128 bit encryption enough or do you need more? | by Lance Gutteridge | Medium

On the Properties of Bit String-Based Measures of Chemical Similarity | Journal of Chemical Information and Modeling

An example of a 36-character string depicting a 128-bit binary value in... | Download Scientific Diagram

How Secret Recovery Phrases Work. Understand the mystical secret words… | by Ernesto Ojeda | Neftify | Medium